Secure communication solutions
Secure Communication Solutions refer to a range of technologies and strategies designed to ensure the confidentiality, integrity, and authenticity of communication channels. These solutions are crucial for businesses and individuals who need to protect sensitive information from unauthorized access or interception.
Secure Communication Solutions are designed to mitigate the risks associated with unauthorized access, data breaches, and eavesdropping, thereby ensuring that sensitive information remains protected during transmission.
In today's interconnected digital landscape, secure communication solutions play a critical role in safeguarding sensitive data, maintaining compliance with regulations, and building trust with customers and partners.
Secure communication solutions encompass a range of technologies and practices designed to protect sensitive information during transmission. These solutions often include encrypted messaging and calling platforms that utilize strong encryption algorithms to secure data, as well as secure email services with end-to-end encryption. Additionally, virtual private networks (VPNs) are commonly used to create secure, encrypted connections over less secure networks, such as public Wi-Fi. Moreover, secure communication solutions may involve secure file sharing, digital signatures, and secure collaboration tools that ensure the confidentiality, integrity, and authenticity of shared data. These solutions are vital for safeguarding sensitive communications and data against unauthorized access and interception.
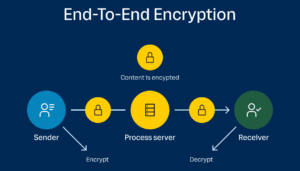
End-to-end encryption (E2EE)
End-to-end encryption (E2EE) is a method of secure communication that prevents third-parties from accessing data while it's transferred from one end system or device to another. In an E2EE system, the data is encrypted on the sender's device or system and only the recipient is able to decrypt it. No intermediate servers, service providers, or other entities can access the plaintext data. This type of encryption ensures that even if the data is intercepted during transmission, it remains confidential and secure. End-to-end encryption is commonly used in messaging apps, email services, and voice-over-IP (VoIP) calling systems to protect user communications from unauthorized access. E2EE is essential for maintaining privacy and security in digital communications, especially when sensitive or confidential information is being shared.

Encrypted phones
Encrypted phones are mobile devices that incorporate advanced security features to protect the privacy and confidentiality of communications and data. These devices use robust encryption algorithms to secure voice calls, text messages, and other forms of communication, making it extremely difficult for unauthorized parties to intercept or access the encrypted information. In addition to encrypted communication, these phones often include features such as secure boot processes, hardware-based encryption, and protection against tampering and eavesdropping. Some encrypted phones also offer secure storage for sensitive data and the ability to run apps in a secure, isolated environment. Encrypted phones are commonly used by individuals and organizations that handle sensitive or confidential information and need to ensure the highest level of privacy and security for their communications and data.




